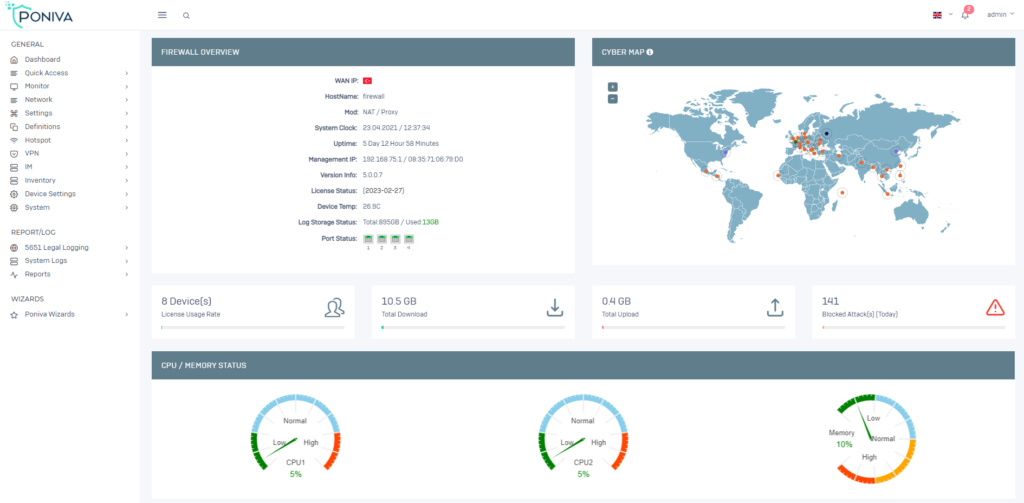
EASY MANAGEMENT.
Prevent Attacks with High Threat Protection Performance.
Provide comprehensive threat protection to your business, including web filtering, malware protection, and application control
Protect from attackers with more than 10 million IPs and constantly updated.
CYBER SECURITY.
Cyber security is the protection of systems connected to the Internet, including hardware, software and data, against cyber attacks.
Security in the context of computing includes cyber security and physical security. Both are used by businesses to protect against unauthorized access to data centers and other computerized systems.
Information security, designed to protect the confidentiality, integrity, and usability of data, is a subset of cyber security.

CYBER SECURITY BUILDING STONES.
Cyber Security has 3 most important building blocks.
People
Process
Technology
PEOPLE.
Every employee should be aware of their role in preventing and mitigating cyber threats, and expert technical cyber security personnel should be fully aware of the latest skills and qualifications to mitigate and respond to cyber attacks.
All transactions on the Internet should be careful. They try to be successful by taking advantage of people’s carelessness in attacks such as e-mail and so on.
PROCESS.
Cyber threats are changing rapidly, so processes need to be constantly reviewed to adapt to them.
TECHNOLOGY.
By identifying the cyber risks your organization faces, you can start looking at what controls to implement and what technologies you need to do. Depending on your risk assessment and acceptance as an acceptable level of risk, various technologies can be used to prevent or reduce the impact of cyber risks.
TYPES OF CYBER SECURITY THREAT.
The process of adapting to new technologies, security trends and threat intelligence is a difficult task. However, it is necessary in a variety of ways to protect information and other assets from cyber threats.
RANSOMWARE.
It is a type of malware that involves an attacker locking computer system files (usually through encryption) and requesting a payment to decrypt and unlock them.
SOCIAL ENGINEERING.
Social engineering is an attack based on human interaction (deception, etc.) to obtain users’ sensitive information.
MALWARE.
Malware is any file or program used to harm a computer user, such as worms, computer viruses, Trojans, and spyware.
PHISHING.
It is a form of fraud in which fraudulent e-mails are sent that resemble e-mails from trusted sources; however, the purpose of these emails is to steal sensitive data such as credit cards or login information. In addition, through dangerous links in these mails, they can get your data by installing programs on your computer from you.

YOU BE PROTECT AGAINST CYBER ATTACKS WITH PONIVA FIREWALL.
When an organization has a strong network security awareness and an effective incident response plan, these attacks are easier to prevent and mitigate. Cyber attacks against stey one step ahead with Poniva Firewall!
DON’T DROWN IN COMPLEXITY.
Firewall management has never been easier, as fast as it’s easy! It does not hold you in the process and gives instant answers.